Microsoft has blocked the ability to download files using Windows Defender after it was shown how easily it could be used by attackers to install malware onto a computer.
Earlier this year, for reasons yet unclear, Microsoft discreetly added the ability to download files using Windows Defender. When this was publicly recognized, there was grave concern from many in the cybersecurity industry that Microsoft had opened up Defender to be abused by attackers as a LOLBIN or living-off-the-land binaries. These are legitimate operating system files that can be abused for malicious purposes.
To download a file, users were allowed to run the Microsoft Anti-Malware Service Command Line Utility (MpCmdRun.exe) with the -DownloadFile argument, as shown here:
MpCmdRun.exe -DownloadFile -url [url] -path [path_to_save_file]Code language: PowerShell (powershell)In cyber security tests, users were able to download any file, including ransomware, into Windows systems through this path. This meant, if active, Windows Defender could quickly detect the malware, but if inactive other security software that many Windows programs use were prevented from detecting the download.
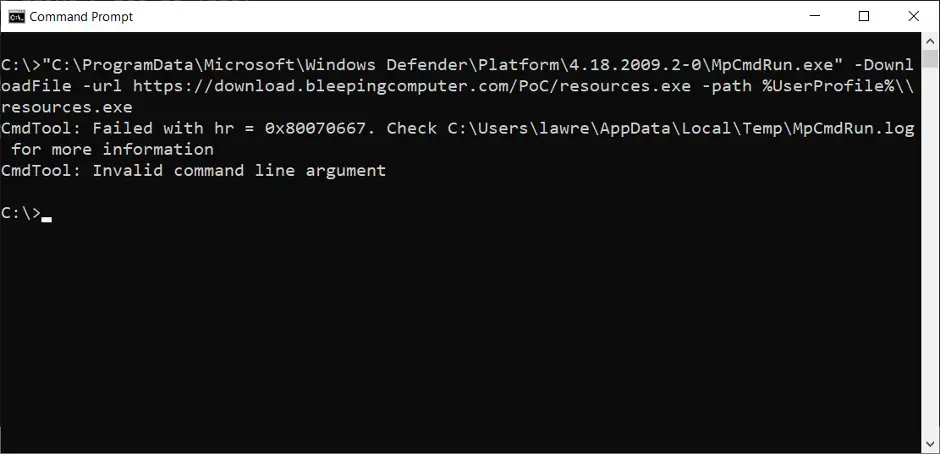
In the later release of the Windows Defender Antimalware Client version 4.18.2009.2-0, it was discovered that Microsoft had again stealthily changed the MpCmdRun.exe features. This time, removing the ability to download files via the MpCmdRun.exe command-line utility.
Users who now attempt to download a file using MpCmdRun.exe will receive an error showing “Invalid command line argument.” The -DownloadFile command line option has been removed from the help screen.
It is hard to understand why Microsoft would have included the option in the first place. Threat actors will use every tool they can find, especially ones that are automatically allowed, such as Window binaries.
Using LOLBINs in attacks has been used in the past by the TA505 APT group, ransomware attacks, and other malware attacks. Removing this option from Windows Defender was a good thing – credit must be given to Microsoft for reacting quickly once it had been identified. But, it makes no sense giving threat actors additional tools to compromise systems, so the question remains: How did it happen in the first place? Microsoft have declined to comment on the addition or subsequent removal of this option.