Security researcher Jimmy Bayne (@bohops) has revealed that specially crafted Windows themes can be used to perform Pass-the-Hash attacks and steal passwords. Pass-the-Hash attacks are used to steal Windows login names and password hashes by tricking the user into accessing a remote SMB share that requires authentication.
A theme’s settings are saved under the %AppData%\Microsoft\Windows\Themes folder as a file with a .theme extension, such as ‘Custom Dark.theme.’ Windows themes can then be shared with other users by right-clicking on an active theme and selecting ‘Save theme for sharing,’ which will package the theme into a ‘.deskthemepack’ file. These desktop theme packs can then be shared via email or as downloads on websites, and installed by simply double-clicking them.
When trying to access the remote resource, Windows will automatically try to login to the remote system by sending the Windows user’s login name and an NTLM hash of their password. In a Pass-the-Hash attack, the sent credentials are harvested by the attackers, who then attempt to dehash the password to access the visitors’ login name and password.
In a test previously done by BleepingComputer, dehashing an easy password took just less than 5 seconds to crack.
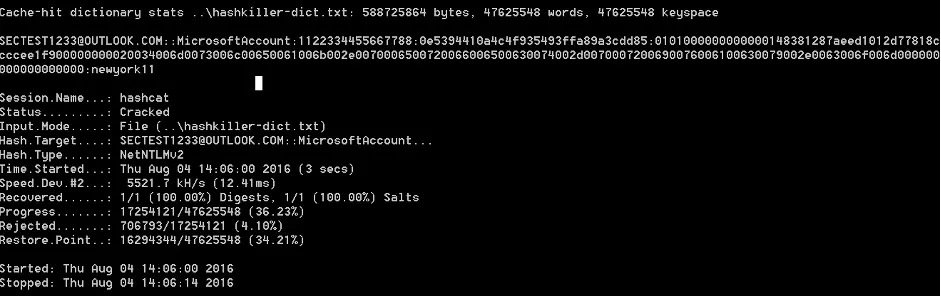
In the new method discovered by Bayne, an attacker can create a specially crafted .theme file and change the desktop wallpaper setting to use a remote authentication-required resource. When Windows tries to access the remote authentication-required resource, it will automatically try to log into the share by sending the NTLM hash and login name for the logged into an account. The attacker can then harvest the credentials and dehash the password using special scripts, so it is in a clear text form.
As Pass-the-Hash attacks will send the account used to login to Windows, including a Microsoft account, this type of attack is becoming more problematic. Since Microsoft is moving away from local Windows 10 accounts and towards Microsoft accounts, remote attackers can use this attack to more easily access the many remote services offered by Microsoft. This includes being able to potentially access email, Azure, or accessible corporate networks remotely.
Bayne stated that he disclosed this attack to Microsoft earlier this year but was told it would not be fixed as it is a “feature by design.”
Bayne advised that the only safe way to protect against malicious theme files, is to block or re-associate the .theme, .themepack, and .desktopthemepackfile extensions to a different program.
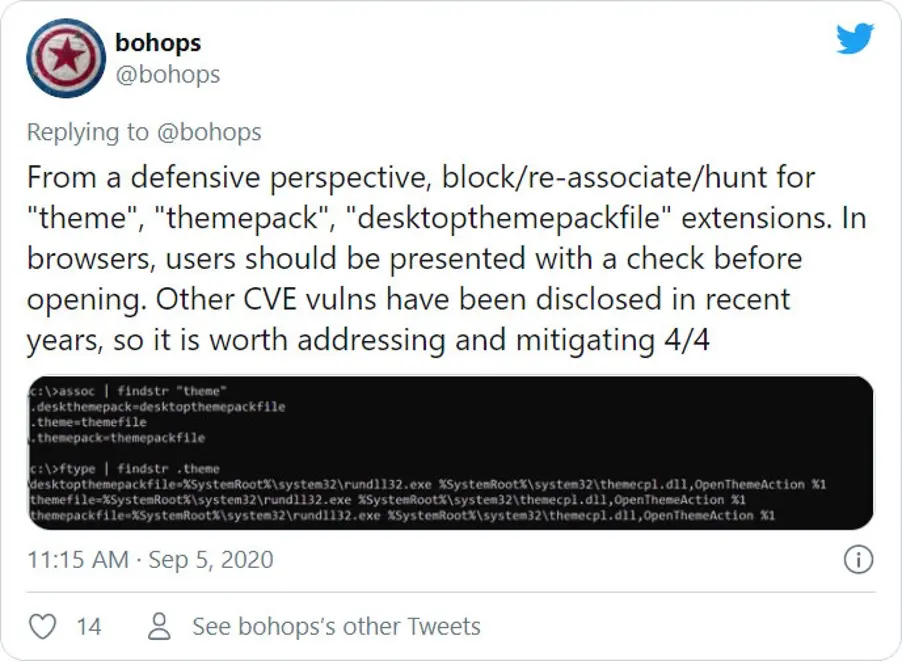
Doing so, though, will break the Windows 10 Themes feature, so only use it if you do never need to switch to another theme.
Windows users can configure a group policy named ‘Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers’ and set it to ‘Deny All’ to prevent your NTLM credentials from being sent to remote hosts.
However, configuring this option can cause issues in enterprise environments that use remote shares. Bayne also suggested adding multi-factor authentication to Microsoft accounts to prevent them from being accessed remotely by attackers who could successfully steal the login credentials.







