In this tutorial we will explain how you create a SSH Key pair and how to use this key to authenticate on remote devices.
SSH, that stands for Secure Shell, is a network protocol used to establish an encrypted connection between two devices. The SSH protocol supports either the use of a username and password combination, or the use of public key cryptography for authenticating hosts and users.
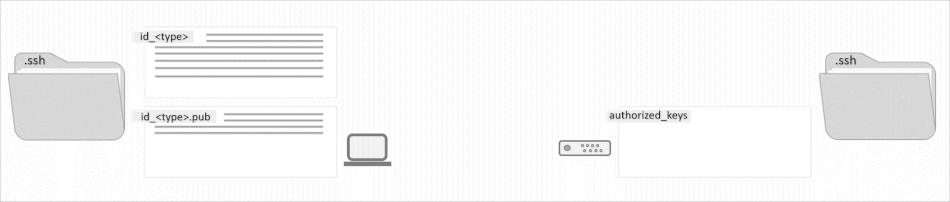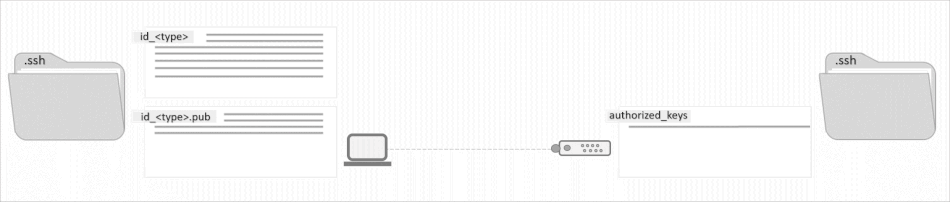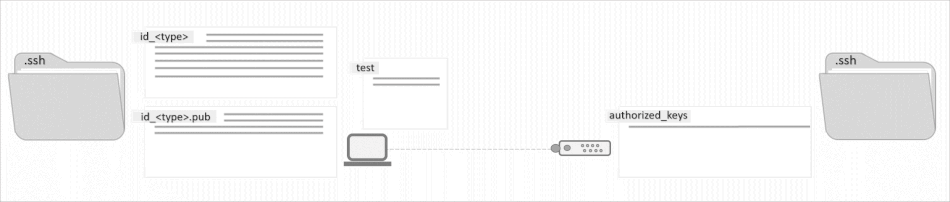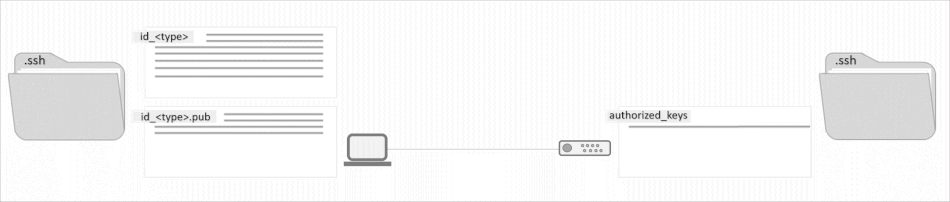
The SSH Key has two pair components: a private key and a public key. Only a private key can decrypt messages that have been encrypted with its pair public key. The public key is the shareable part of the pair, which is saved on the devices which you want to access.
On the other hand, as the name suggests, the private key is private and should not be shared with anyone. In nature SSH Keys are authentication credentials just like passwords, which means should be managed carefully.
Algorithms and Key Size
SSH supports several different key algorithms for authentication keys. These include:
- RSA – RSA (Rivest-Shamir-Adleman) is a widely used public-key algorithm widely used on data transmission, and also one of the oldest. The acronym comes from the surnames of its creators, who described the algorithm in 1977. The security of the RSA algorithm relias on the practical difficulty of factoring the product of two large prime numbers, also known as the “factoring problem”. RSA is a relatively slow algorithm, and because of this it is not commonly used to encrypt user data, instead RSA is used more commonly to transmit shared keys for symmetric key cryptography;
- DSA – this is an old US government Digital Signature Algorithm. It is based on the algebraic properties of modular exponentiation together with the discrete logarithm problem, which is considered as computationally intractable. This algorithm was proposed by the National Institute of Standards and Technology (NIST) in 1991 as response to a solicitation from the US government for a public key signature standard. It is to be replaced by newer signature schemes such as EdDSA;
- ECDSA – The acronym stands for Elliptic Curve Digital Signature Algorithm, a new Digital Signature Algorithm standardised by the US government, and uses elliptic curves. Only three key sizes are supported: 256 bit, 384 bit and 512 bit. Most SSH clients now support this algorithm;
- Ed25519 – this algorithm uses the EdDSA scheme with SHA-512 (SHA-2) and Curve25519. EdDSA stands for Edwards-curve Digital Security Algorithm, a digital signature scheme using a variant of Schnorr signature based on twisted Edwards curves. It’s designed to be faster than existing digital signature schemes without sacrificing security. This is one of the most recent algorithms added to OpenSSH, and support in clients is not yet universal, tho it is currently one of the most recommended algorithms.
The most common type of key used is an rsa key. Today, we should preferably use a more secure algorithm like ed25519. We will demonstrate how to create both.
How to create a SSH Key – old method
To select the algorithm we’ll use the -t option. To choose the key size, in bits, you must use the -b option, and we can also add a comment (to identify the key or key owner). To generate a key using the rsa algorithm and 2048 bit size, you may use the following command:
ssh-keygen -t rsa -b 2048 -C "[email protected]"Code language: Bash (bash)When asked to enter passphase, just hit enter to proceed without one. Unless otherwise specified, the key will be stored at your user home directory in the .ssh folder. Listing the contents of your .ssh directory you’ll find two files, id_rsa corresponding to the private key, that you should never share, but keep it secured, and id_rsa.pub, the public key, that is to be installed on the remote machines.
ls ~/.ssh/id_rs*
-rw------- 1 admin staff 1766 Nov 29 2015 .ssh/id_rsa
-rw-r--r-- 1 admin staff 403 Nov 29 2015 .ssh/id_rsa.pubCode language: Bash (bash)How to create a SSH Key using the ed25519 algorithm
We must keep in mind that older ssh clients may not support ed25519, as it is a more recent and secure format. Also, when creating a ssh key using the ed25519 algorithm, there is no need to set the key size, as all ed25519 keys are 256 bit. This is due to the completely different type of cryptography being used, and therefor, has the same security at different key sizes. One could say, it’s not about size!
ssh-keygen -t ed25519 -C "user@hostname"Code language: JavaScript (javascript)These keys will also be stored inside the .ssh folder at your user home directory. Check them out:
ls -la .ssh/id_ed*
-rw------- 1 admin staff 464 Nov 25 21:06 .ssh/id_ed25519
-rw-r--r-- 1 admin staff 96 Nov 25 21:06 .ssh/id_ed25519.pubEnter passphrase (empty for no passphrase)
Securing the SSH key with a password depends largely on the usage intended for the SSH key. SSH keys for users should be protected by a passphrase. That way, if anyone is able to start a session with your user, or even get access to the private keys, they won’t be able to use it.
However, SSH keys can also be used to automate several tasks, like ansible or even to copy backups over to a remote server. If no user interaction is expected when using the keys, the passphrase should be left empty.







