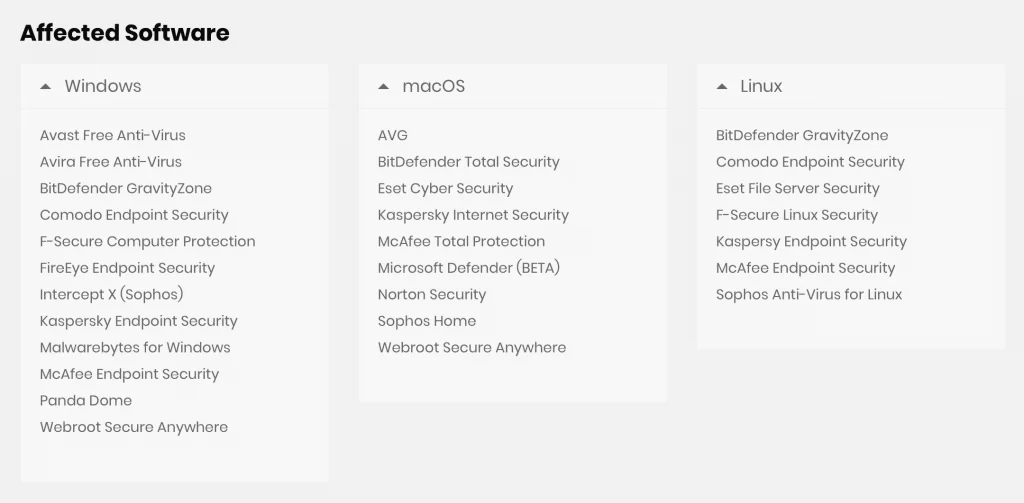
According to a report published this week by security researchers from RACK911, “symlink race” vulnerabilities were found in 28 of today’s most popular antivirus software.
RACK911 Labs reports how they came up with a simple method of using directory junctions (Windows) and symlinks (macOS & Linux) to exploit the most popular antivirus programs.
A symlink race is a software vulnerability is where programs get to create files in insecure manners, allowing to create symbolic links to resources otherwise not accessible. This allows malicious agents to alter the linked-to file contents, and the execution of rogue code.
On Windows, the exploit is attained by using directory junctions, an exclusive of this operative system that links two directories together, which can be performed by any user and doesn’t require administrator privileges.
By using this vulnerability an attacker is able to mess with the system in many different ways, from making the antivirus software useless to removing key operating system files and breaking the system.
The report notes the security research team primary focus on the capabilities of destructive behaviours using this exploits, however, these exploits also allowed to target files and directories, changing permissions and ownerships, all which could lead to a more severe impact on the compromised systems.
A privileged malicious agent
Almost all antivirus software requires privileged access to the operative system, which means almost all file operations are performed with high levels of authority within the system.
The report also mentions the simple nature of the exploit, and how easy would be for malware authors to take their endeavours forward:
“Make no mistake about it, exploiting these flaws were pretty trivial and seasoned malware authors will have no problem weaponizing the tactics outlined in this blog post. The hardest part will be figuring out when to perform the directory junction or symlink as timing is everything; One second too early or one second too late and the exploit will not work.
With that said, a local malicious user who is attempting to escalate their privileges would be able to figure out the correct timing with little effort. In some of the antivirus software that we exploited, timing wasn’t important at all and a simple loop statement of running the exploit over and over was all that was needed to manipulate the antivirus software into self-destructing.”
According to the same report, RACK911 Labs started notifying antivirus vendors in the fall of 2018 about these vulnerabilities. While most of the vendors have fixed their products, there are still exceptions. Given the media attention to the issue, it is expected that the few who haven’t addressed the vulnerability will do it shortly.