macOS security and com.apple.quarantine extended attribute
Apple offers one of the most advanced operating systems out there: macOS. With security and privacy in its core, it comes with a number of system protection services such as Gatekeeper runtime protection, the built-in System Integrity Protection (SIP), and others. While Apple Software, Apple installers and apps from the App Store are already cleared […]
Upgrade RAID1 to RAID5 without losing data

Initial considerations It is possible to upgrade RAID1 to RAID5 without losing data, but as any operation that involves stored data it is dangerous and may result in dataloss if not performed correctly, so be warned. Please be aware that this operation requires a Disk ARRAY of N-disk where N ≥ 3. The process to […]
Using OpenSSL to verify SSL/TLS connections

OpenSSL is a general-purpose cryptography library and full-featured toolkit for the Transport Layer Security (TLS) and Secure Sockets Layer (SSL) protocols. It’s licensed under the Apache License 2.0, meaning that you are free to get and use it for both commercial and non-commercial purposes, subject to a few simple license conditions. Using OpenSSL to check […]
PHP-FPM settings for best performance

A recurring question we get from customers is how to fine tune PHP-FPM settings. The official PHP documentation kind of lacks recommendations in this regard. So we’ve made this article explaining how you can calculate the optimal PHP-FPM settings for your server. PHP-FPM is an acronym for PHP FastCGI Process Manager, one of the most […]
Install docker & docker-compose on Oracle Linux

By default on the new Enterprise Linux distributions, docker engine has been replaced by podman, a docker compliant engine. In order to install docker and docker-compose, you can follow this simple tutorial. Install Docker Engine To install docker engine we’ll add first the docker repository: And now we can proceed to install docker: And we […]
How to mount a VHD disk image file

Sometimes you may need to mount a VHD disk image file in order to inspect its contents or even recover specific files. On Linux you can use the QEMU Disk Network Block Device Server utility – qemu-nbd – to access disk images in different formats as if they were block devices. First, you may want […]
How To Create a SSH Key

In this tutorial we will explain how you create a SSH Key pair and how to use this key to authenticate on remote devices. SSH, that stands for Secure Shell, is a network protocol used to establish an encrypted connection between two devices. The SSH protocol supports either the use of a username and password […]
Build MTR from source on macOS
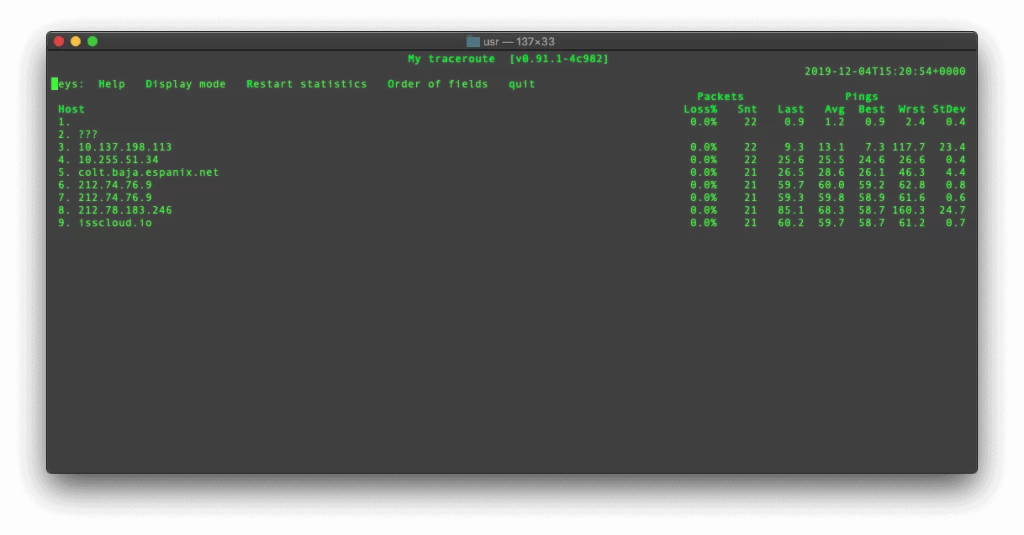
MTR, or “My Traceroute” (originally named Matt’s Traceroute after its original creator Matt Kimball) is an amazing network diagnose tool that combines the functionality of both ‘ping’ and ‘traceroute’ into one single program. It determines the route and address of each hop between the source and destination, and sends a sequence of ICMP ECHO requests […]
How to solve ‘DB_RUNRECOVERY: Fatal error, run database recovery’ in CentOS
While rolling out updates on some servers, and without apparent reason, as yum hadn’t failed or thrown any errors before, it failed with DB_RUNRECOVERY: Fatal error, run database recovery: YUM is failing and not accepting any command. While the reason for my YUM database corruption isn’t known, the solution is quite simple and easy to […]
CentOS 7 – Install And Configure ClamAV
Clam AntiVirus (commonly ClamAV) is a free, cross-platform and open-source antivirus software toolkit able to detect many types of malicious software, including viruses. One of its main uses is on mail servers as a server-side email virus scanner. Despite the myth, Linux operative systems do get troubled with Virus. They can take down your website, […]
