Google’s Android Lockbox spying competitor apps

Revelations have emerged from reported sources that Google is spying on how people interact with rival Android apps. The report mentions how Google is monitoring users interactions with non-Google apps via an internal program and utilizing the data to improve its own products. According to a startling report in The Information, a program called Android Lockbox gives […]
NSA and FBI warn about national security threat due to new Linux malware

The United States the National Security Agency (NSA) and Federal Bureau of Investigation (FBI) have taken the unusual step of publishing a joint security alert containing details about a new strain of Linux malware that the agencies claim was developed and deployed in attacks by Russian military hackers. Through their joint alert, the two agencies […]
Security issues surface as employees use personal computers to Work from Home

The global Covid-19 pandemic forced many businesses to rapidly relocate employees from the office to working from home. For many organizations this meant enacting, and exposing weaknesses, in their emergency plans created to continue business in the event of fire or flood. Most of these back-up plans centered on protecting data and setting up a temporary workplace […]
Work from Home employees ignoring security guidelines

Cybersecurity has always been a big priority in IT but the global pandemic has invoked endless extra headaches for IT managers as remote working became a necessary routine around the world. According to a new study many organizations, despite having good practice and awareness embedded in an office environment, discovered that employees quickly slipped into […]
Developers ignoring software testing automation

A tough, agile system strategy is critical to all organizations but, according to a new survey, less than 80% of developers are automating fewer than half their tests. Proper software testing ensures the launch of a new software system can implement smoothly and is an essential tool for project managers. The operation of any software […]
UPnP vulnerability allows attackers to scan internal networks and steal data

Latest research has revealed that the Universal Plug and Play (UPnP) network protocol has an integral security flaw that leaves printers, routers, and millions of other devices wide open to an attack which can remotely commandeer them. The UPnP protocol has been in use since 2008 predominantly but not exclusively being installed on routers. It allows devices […]
Bluetooth flaw allows device impersonation
A Swiss research institute has uncovered yet another vulnerability in Bluetooth protocol that leaves millions of devices open to attack. Last year the same team of researchers revealed what they called a “novel and powerful” Key Negotiation of Bluetooth (KNOB) attack that impersonated the receiver of sensitive files and transmitted encrypted commands to unlock a […]
Lenovo ThinkPad will offer Linux pre-installed

According to an announcement published by Matthew Miller, Fedora Project Leader, on the popular website Fedora Magazine, new Lenovo ThinkPad laptops with Fedora Workstation pre-installed will be available in a near future. It is a pilot of Lenovo’s Linux Community Series – Fedora Edition, that begins with ThinkPad P1 Gen2, ThinkPad P53 and ThinkPad X1 […]
28 Antivirus products affected by symlink race bugs

According to a report published this week by security researchers from RACK911, “symlink race” vulnerabilities were found in 28 of today’s most popular antivirus software. RACK911 Labs reports how they came up with a simple method of using directory junctions (Windows) and symlinks (macOS & Linux) to exploit the most popular antivirus programs. A symlink […]
Build MTR from source on macOS
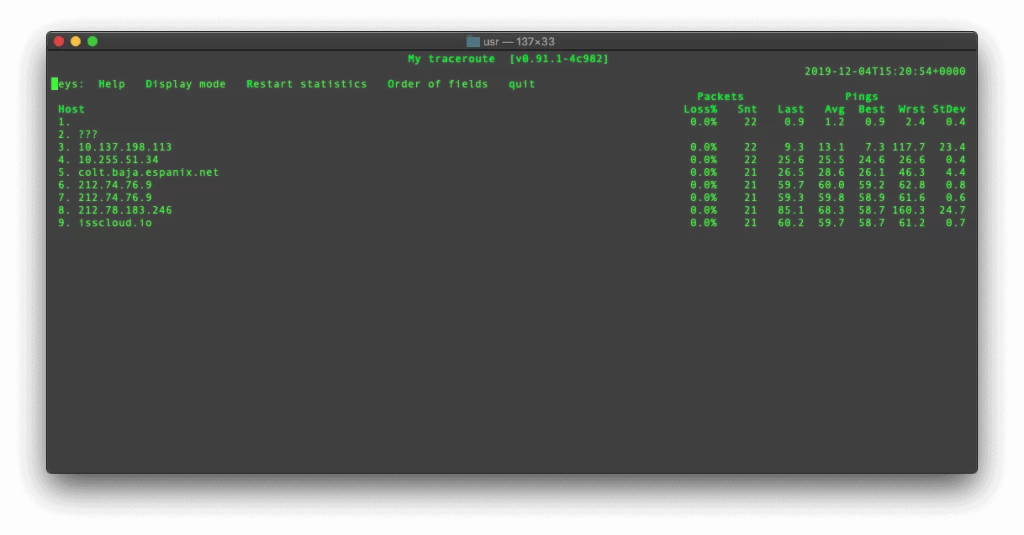
MTR, or “My Traceroute” (originally named Matt’s Traceroute after its original creator Matt Kimball) is an amazing network diagnose tool that combines the functionality of both ‘ping’ and ‘traceroute’ into one single program. It determines the route and address of each hop between the source and destination, and sends a sequence of ICMP ECHO requests […]
